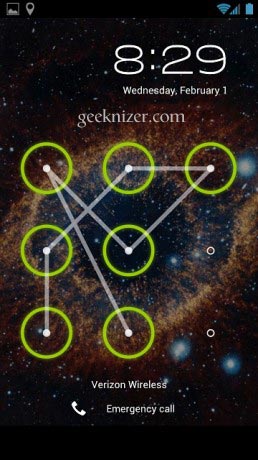
We know the pain you can go through when you forget Android Lockscreen pattern.
Truth be told, Android’s Lockscreen pattern provides high security, even FBI has trouble unlocking it. From the Wired article:
The bureau claims in federal court documents that forensics experts performed “multiple attempts” to access the contents of a Samsung Exhibit II handset, but failed to unlock the phone.
So how do you Unlock something which is so secure? One obvious way is to look for smudges in the screen reflection and you might see the pattern. But its not always easy. Read on to find out how you can bypass Lockscreen pattern in a more reliable way.
If you try to unlock the pattern with too many attempts, device locks down unless you enter the Google account password to restore the state.
How to Bypass / Unlock / Recover Android LockScreen Pattern
This system is secure altogether, the underlying encryption makes sure it works. But there are always Loopholes to everything. What if you can disable the pattern via ADB console?
Warning: You must use this hack in case you lost access to your phone, don’t be unethical
Note: The Method works on both Rooted and Non-rooted devices. Its more reliable to do on Rooted phone, we’re not sure if it would work on non-rooted phones. However, it requires that phone’s USB debugging mode is enabled before its locked down with a pattern. If you don’t have it enabled, there’s still hope, read the tip at the end of the post.
We demonstrate the method to unlock a locked, forgotten Pattern, it requires you to have:
- Android SDK (ADB executable)
- Adb debugging enabled on device (if not, read tip at the end of the post)
- USB cable.
- Rooted phones (Chances increase that it will get through)
Step 1.
adb shell cd /data/data/com.android.providers.settings/databases sqlite3 settings.db update system set value=0 where name='lock_pattern_autolock'; update system set value=0 where name='lockscreen.lockedoutpermanently'; .quit
when done, reboot.
Step 2:
adb shell rm /data/system/gesture.key
Reboot when done.
Step 3. When device reboots, you will still see a pattern lock screen. But here’s the catch: just try any random pattern and it may unlock then remove the pattern from settings.
Tip for Rooted users who forgot to have USB debugging enabled: If you have forgotten to leave USB debugging enabled, reboot your phone into recovery and do the same. No USB debugging required. You may however need to mount the partition being accessed by this method, and you can do that only if you have a custom recovery installed. Just go to ‘Mounts and Storage’ and mount /data. Then use the method just the normal way by manually doing the things commands do.
Disclaimer: Developer claims that it worked for him on Stock AOSP ICS, Jellybean on Galaxy Nexus, this may or may not work with all Android devices. In any case, it’s worth trying when you’re out of luck.
credits: Xda developer m.sabra
We write latest and greatest in Tech Guides, Apple, iPhone, Tablets, Android, Open Source, Latest in Tech, subscribe to us @geeknizer on Twitter OR Google+ or on Facebook Fanpage:
loading...
loading...

ive tried this on my phone; however i think i hit a bit of a snafu. If my phone has locked me out due to too many pattern attempts is all hope lost?
loading...
loading...
droid 4 ICS only the last part was necessary as i did not have SQLlite installed … any random pattern worked and brought me in imminently to selecting pattern … unlocking with my face for months i forgot my pattern!
loading...
loading...
It works very well, thank you!!!
loading...
loading...
could you just adb pull the settings.db update it and then use adb push to put the changed file back in the phone, since my phone didn’t have sqlite3 installed by default?
loading...
loading...
This is extremely disconcerting. Does this not mean that no Android has 100% security? If an attacker can go into recovery mode to enable usb debugging, what’s the point of even turning it off? What’s the point of even locking your phone?
loading...
loading...
i think it’s secure not system … so the 4,5th lines are:
update secure set value=0 where name=’lock_pattern_autolock’;
update secure set value=0 where name=’lockscreen.lockedoutpermanently’;
loading...
loading...
and thanks for the useful tips, it really helps !!!
loading...
loading...